Zoom - New Security & Functionality Features You Need to Know
New settings and features are consistently being rolled out in Zoom. A byproduct of having an overwhelming number of users switch to remote meetings, was how quickly weaknesses and vulnerabilities were exposed by users. In response, Zoom halted production on adding new features to focus on tightening security.
Months have passed since then, and even more updates have been released as people continue to use the product, give feedback, and talk about what works and what doesn't. This post discusses some features that are helpful for participants to know and understand as it helps their meetings be more fluid.
Zoom - New Security & Functionality Features You Need to Know
There are far more settings available in Zoom than can be covered in a single post, so this post will focus on 4 areas:
- Muting participants
- Accessing meetings
- Screen sharing
- Transferring files
Muting participants
There are several ways to mute participants in a Zoom meeting. Meetings can be created with all participants muted upon entry or a host can mute a participant at any time during the meeting.
NOTE: Unlike meetings, webinars are typically set up so that only hosts and co-hosts can speak.
The big change with muting that rolled out in October is the limitation for unmuting an attendee. Once a host mutes someone, or they mute themselves, the host cannot unmute them. Instead, the host can simply click a button to "ask to unmute" the participant. Prior to this update, a host could mute and unmute participants at will.
This was a big shift for any host that regularly helped out participants by unmuting them when the speaker rotated. Unfortunately, there are security risks when a host can unmute a participant at any time. It was possible for someone to be unmuted without being aware of it. Even if the host was unmuting people for the right reasons, it is easy to see how someone on a private call or talking in the background might not want the host to unknowingly unmute them.
The takeaway: Once you are muted, whether by yourself, or via a host, you are the only one who can unmute yourself.
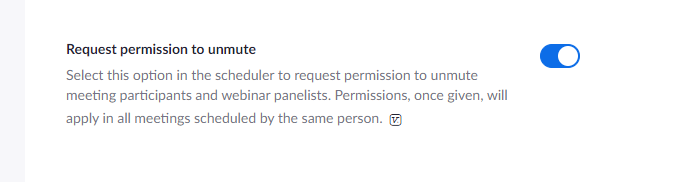
The exception: There is setting called "Request permission to unmute" that can be enabled by a host. Once enabled, any participant that allows a host to unmute you, will be able to be unmuted later by that same host without being asked. In other words, if Host A asks to unmute you and you accept, Host A will be able to unmute you in any future meetings they schedule without asking. As a result, you may want to be cautious about which hosts you allow to unmute you.
Accessing meetings
In earlier versions of Zoom, people could join meetings by clicking a link or entering a meeting with a meeting ID. Users were then prompted to join with video and audio, and once selected, they were in the meeting.
As of October 1st, meeting participants go through an additional step to join meetings. Hosts had the choice of implementing the waiting room feature, or adding a passcode to meetings in addition to the meeting ID. Hosts that had recurring meetings with no end date, found those meetings ended for them. They then had to create a new recurring meeting and the new security criteria was added to that meeting.
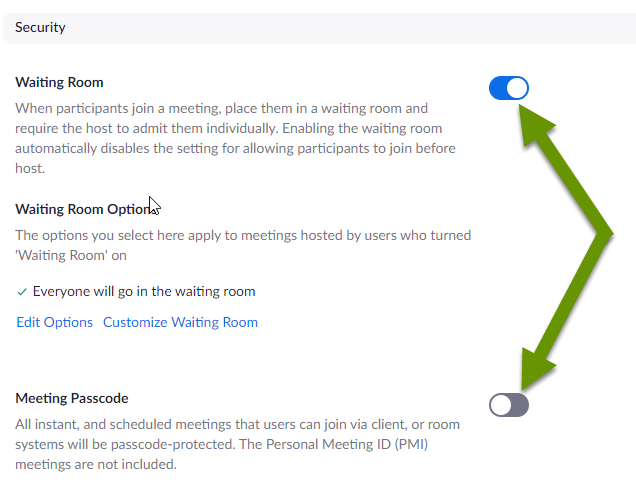
The waiting room operates like a temporary holding area. A participant "joins" the meeting and the host is prompted to allow or deny them access to the meeting. Once allowed, the participant shows up in the meeting normally. Participants do not see these prompts.
Adding a passcode to a meeting works exactly as it sounds. A participant can click the meeting link and enter the passcode, or they can join the meeting by entering the meeting ID and the corresponding passcode.
The takeaway: Smaller meetings will benefit from using a waiting room as the experience is nearly identical for end users. On the contrary, larger meetings and webinars will benefit from a passcode as it can be interruptive and tedious for the host to continue to filter and admit users through the waiting room. Alternatively, utilize additional hosts or co-hosts to help manage the waiting room.
Screen sharing
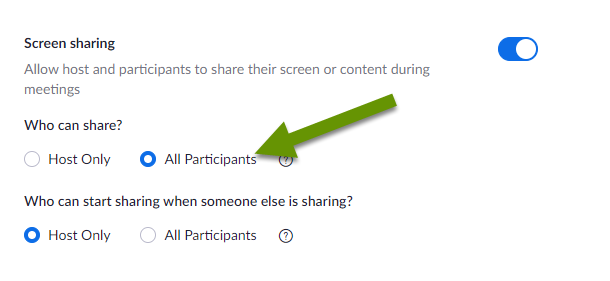
Screen sharing is a great way for participants to show information and other materials to the group. Screen sharing is another example of a feature affected by the October update. The update reverted the settings for screen sharing to "host only". Luckily, the ability to allow participants to screen share is available to hosts at any time during a meeting via the menu panel.
Additionally, the screen share permission can be modified in the settings preferences to allow screen sharing by all participants.
The takeaway: Screen sharing was definitely one of the early features most abused as people shared Zoom meeting info with the world. Luckily, there are now several ways to prevent unknown or uninvited "guests" from joining your meetings. Try using these rather than preventing users from sharing their screens, which can often provide detailed, clear and concise information in a more succinct format.
Transferring files
Last but not least, a host can limit file transfers. This can be limited in multiple ways including:
- Preventing all file transfers
- Allowing only specific file types to be transferred
- Setting a maximum file size on files transferred
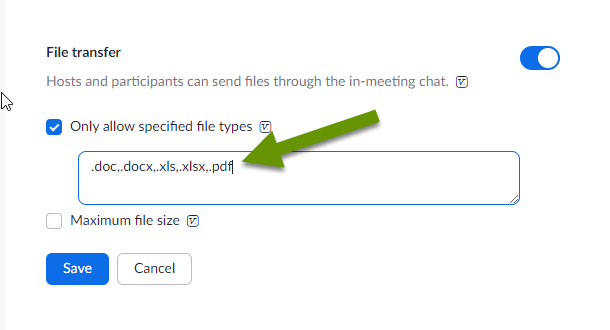
Managing transferred files is one way for hosts to protect participants. For example, listing the types of files to allow while leaving out .exe and similar file types that are more likely to be harmful, provides additional protection for users. Keep in mind, even hosts do not see private chat messages they are not a part of, meaning someone could try to send you a harmful file without the host knowing.
The takeaway: Hosts that configure file transfer settings are probably doing so to protect users. If you have something legitimate to send, try using email or asking the host to share on your behalf.
Zoom can be a great tool for businesses to share information with staff, for groups of people working on a project, and even friends and family to stay in touch. However, like any product, it is best utilized when configured so the security and functionality best meet the needs of the group using it. This post discusses some new aspects of muting, access, screen sharing and file transfers that are helpful for participants to understand.
As always, knowing what settings are available is the best way to set an application to best meet your unique needs!

