What you Need to Know About Last Week's Remote Computer Software Hack
Just before the holiday weekend Kaseya, a tech company that licenses remote management software to managed service providers (MSPs), was hacked. This hack affected approximately 60 MSPs and 1,500 businesses which has led many people to wonder what they can do to protect themselves against an attack of this type.
This post discusses what you need to know about last week's remote computer software hack, how remote connect software should work and what you can do if you think someone is accessing your computer remotely.
What you Need to Know About Last Week's Remote Computer Software Hack
Remote connect software, when used properly, is a fantastic tool. It creates a secure connection between two devices for the purposes of providing technical support without the need to be in the same physical location. In this way, it is a highly efficient tool. For anyone working in IT, they can spend time driving to a user or spend a minute connecting to the user's device and possibly have the issue fixed before they would have arrived at the user's location.
However, there is also a dangerous side to a tool that allows someone you cannot see to connect to your device. Anytime a device can connect to the internet, the flip side is also true - someone can potentially gain access to the device. Remote connect software makes it easier for someone to help you, but when misused, can enable the wrong person to connect to your device.
It can be easy to forget this as most people wonder what they could possibly have on their computer that someone else would want. Unfortunately, there does not necessarily need to be anything enticing on your device. Much like you cannot know what is inside your neighbor's home unless you have been in it, an attacker has no idea what is on your computer until they connect.
In this way, gaining unauthorized access to someone's computer is an odds game for attackers. Even if you do not have anything of value, you know other people who know other people, and on and on. When malware infects, the goal is that it will continue to spread and will eventually run into information the attacker can use against others or that is in itself valuable.
Last week's incident proved how vulnerable tools can make us at times, even when they are extremely useful. In this instance, attackers exploited a zero-day vulnerability to bypass the authentication of Kaseya's remote connect product. Once authenticated with the system, attackers were able to execute code that distributed ransomware to clients of the MSPs that used Kaseya's product to deliver support to their clients.
NOTE: A zero-day vulnerability is a known vulnerability that does not yet have a patch, which is what makes them so dangerous.
Types of remote connect software
For a remote connect software to work, a small piece of software needs to be installed on the end user device. The software creates an encrypted connection between the user and the support provider. The support provider typically connects using a web interface. There are two versions of the software that are downloaded onto the end user device. These include:
- A one-use version that installs a small version of the software locally that can be removed at any time. It does not allow tech support to reconnect once the original session has ended.
- A long-term support version that once installed, allows tech support to connect as needed. The software installed in this version runs in the background at all times. A support provider can reconnect with this version as the software keeps the device available for connections. However, a support person would still need the end user's credentials to log into the local user profile to do most things. This is another great reason NOT to give anyone your credentials.
While both versions require the end user install a small executable, the first version requires interaction by the user each time, requiring codes, to get the support provider connected. Anyone who has signed up for an account with an MSP will most likely have the second version installed, which does not require secondary interaction other than the user being logged in. This is another reason why users should always lock their devices when they walk away.
NOTE: If you allow someone to connect to your device using the one-time version, they can install the long-term version that listens in the background without your interaction or knowledge. Most remote connect software versions come with the ability to silently install their software once connected to any remote device. Again, this is done to make the end user experience better, but it is something every user should know about before allowing someone they do not know to connect to their device.
How remote connect software works
Regardless of which version of remote connect software you have installed on your device, you will often know when someone connects to your computer. Based on how the software is configured, you may be alerted when someone connects, you may receive a pop-up notification in the taskbar, and at the very least, you should see your cursor moving across the screen as they take control of the device.
Unfortunately, there are ways to disguise what is being done. For instance, when people use remote connect software for the wrong reasons, they often:
- Disable the notification feature that informs users they have connected to their devices.
- Disable the taskbar notifications informing users they have connected.
- Connect "in the background" where they can run utilities via the command line window without the end user seeing what is going on.
- Disable the keyboard and mouse on the local device so users cannot disconnect them or stop them from connecting or doing things to the device.
NOTE: There is always something you can do, so read below to find out what you can do if you think someone is accessing your device.
What you can do if someone you did not authorize connects to your device
If you see your mouse cursor moving, and you are not touching or moving your keyboard, mouse or touchpad, there are some things you can do immediately to regain control of your device. Be aware, rebooting the device is NOT enough - the software will simply reconnect the attacker.
On a laptop device:
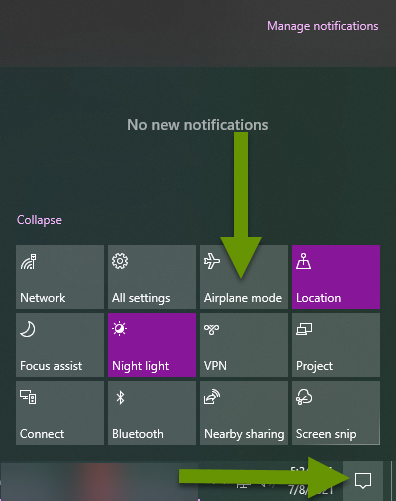
- If the laptop is connected to the internet using a WIFI connection, disable the wireless using a physical button if one exists. In the absence of a physical button, click the keyboard button to disable the wireless if one exists. If those are not available, click on the notification icon in the lower right corner of the taskbar and click on "Airplane mode" to disable all wireless connections. If none of those are available or fail to break the connection, press and hold the power key for 10 seconds to turn the laptop off.
- If the laptop is connected to the internet on a wired connection, disconnect the network cable from the device or dock.
On a desktop device:
- If the computer is on the wireless, click on the notification icon in the lower right corner of the taskbar and click on "Airplane mode" to disable all wireless connections.
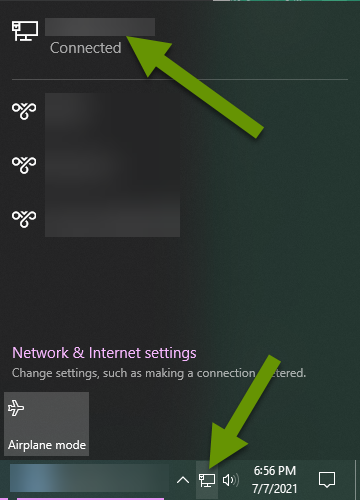
- If the computer uses a wired connection and the network cable is easy to access, disconnect it from the device. Otherwise, click on the network connection icon in the right portion of the taskbar. Click the name of the network the device is connected to which will open the network settings window.
- Right-click on the connected network connection and select "Disable".
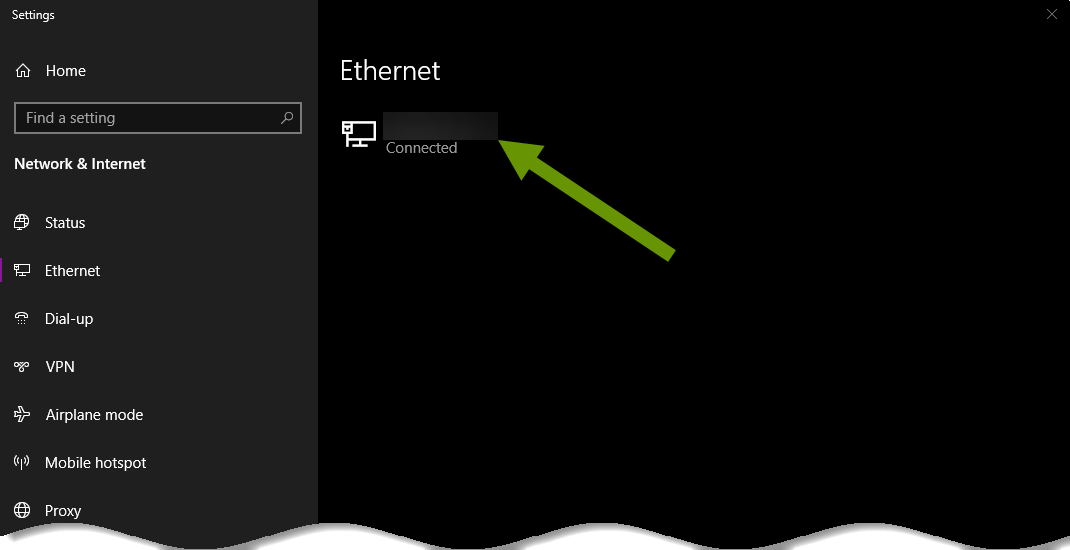
NOTE: You will have to navigate to this setting again later and right-click on the connection to select enable to get it working again. It is best to wait until after you have cleaned up the machine to do this.
- If none of these breaks the connection, press and hold the power button for 10 seconds to power off the device.
Once the device has been shut down and nobody else is connected to it, turn it back on without connecting it to the internet. Run endpoint protection software and remove any potentially unwanted programs. Check for malware using Programs & Features in the Control Panel as well as Apps in the Settings menu. Research anything you suspect to be malware and remove any programs that should not be installed.
NOTE: If you are not comfortable with the steps above, take your device to someone or somewhere you trust.
Receiving remote tech support is extremely handy when you need something fixed. When you only need a simple fix, this software can enable that to happen much faster than waiting for someone to physically get to your location. Also, it is always easier to fix an issue you can see than it is to have someone describe it so you can picture it, then walk them through fixing it!
Unfortunately, this newest hack shows how vulnerable this software can make our devices so be cautious allowing anyone to remote connect to your devices. If you have remote connect software installed that is no longer being used, remove it from your device. Lastly, don't share your credentials with anyone else and lock your devices when you walk away if you leave them powered on.
As always, everything that makes our lives easier also introduces vulnerabilities so stay informed and stay safe!

