Security Warning: Hackers Exploit Outlook and O365 Rules not Syncing
With more people than ever working from home, people are relying upon new forms of communication to accomplish the same tasks. For instance, working in an accounting department likely gave you the ability to quickly and easily confer with a coworker about a new vendor, outstanding bills or updates on client payments. Now, more requests are coming to users directly, pushing them to make decisions in a vacuum which is providing ways for hackers to take advantage.
A prevalent security hack happening right now utilizes email rules. Once an email account is hacked, offenders are able to create email rules to wreak havoc on that account. A flaw between Outlook and Outlook.Office.com webmail creates additional issues. This post discusses how to check both places if your email has been hacked or you are concerned it has been.
Security Warning: Hackers Exploit Outlook and O365 Rules not Syncing
One of the most common security attacks is phishing attacks. These typically come in the form of emails, hoping to get you to click on links or install malware which then can provide access to email, the device, keystrokes, or data. Right now, these attacks are being combined with a flaw in syncing between Outlook and Office.com webmail.
The current phishing attack targets the recipient's email account, and then in turn their contacts and their email accounts. Once a recipient clicks on the malicious link, the hacker is able to access your email. From there, they can do things like:
- Harvest the names and emails of everyone you communicate with.
- Send emails on your behalf using your actual email address.
- Delete emails, like incoming or sent emails, so you might not notice the issue is happening.
- Request and collect payments from your clients and funnel funds to their accounts.
- Add rules to modify the way your email behaves. This can include hundreds of changes including especially dangerous rules like forwarding a copy of every incoming or outgoing email and deleting emails once they are clicked on, etc.
- Possibly worst of all - forward emails with bad links to your contact list in hopes of perpetuating this attack!
It goes without saying that as we continue to work from home, we need to be even more diligent about opening emails and clicking on links. A quick refresher of the best ways you can protect yourself when it comes to emails are to:
- Delete emails from unknown senders.
- Verify a hyperlink destination before clicking it to make sure it is going to an expected website (see image example below).
- Check for misspellings within the sender email address, links inside the email or other content. This is a trick often capitalized on by hackers.
- Most importantly, contact the sender directly if you are even slightly concerned about the validity of the content. This can mean going directly to their website to look for alerts or contact information, creating a new email to the sender so you know you are sending to the correct person, or making a phone call to verify the email is legitimate. Calling to verify is advised anytime you are requested to make an online payment to prevent funds from going to the wrong recipient.
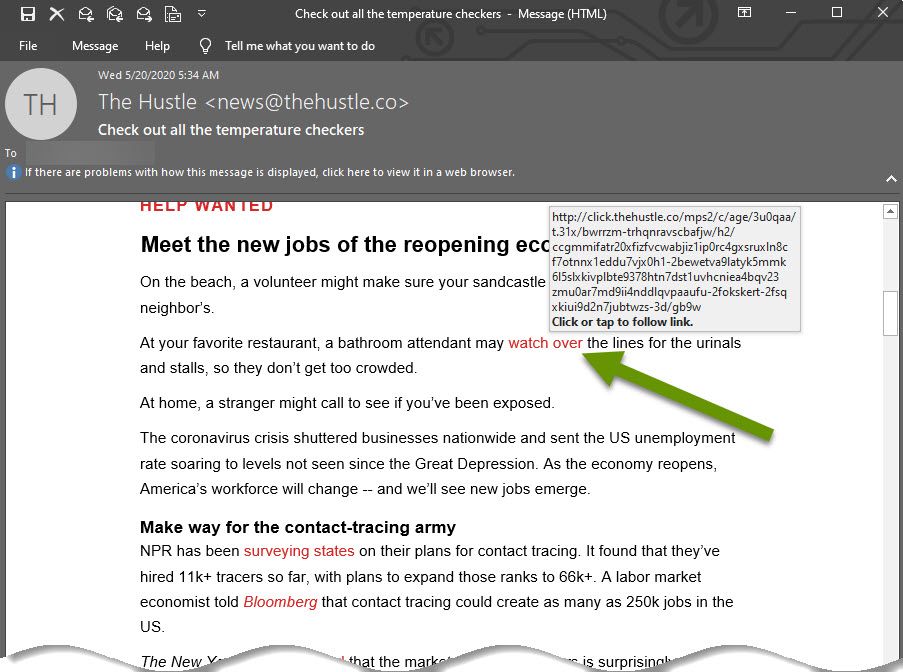
In the image above, I hovered over a link in an email from The Hustle. The link, which is only identified as "watch over", tells me relatively little about where the link will actually take me. However, in the defense of email marketing and materials, including long links in the middle of emails can feel clunky and takes away from the flow of the email so this is often not done for nefarious reasons.
Luckily, hovering over a link shows the destination information and as you can see in this example, the destination is a valid thehustle.co link. It is always a good idea to verify hyperlink destinations before clicking. Taking this one small step is one of the greatest, and easiest, ways you can protect yourself.
If you happen to click on a malicious link and think your email may have been hacked, or you are witnessing oddities like disappearing emails, etc., follow the steps below to protect your device, data and contacts.
Step 1: Change your password!
The first thing you need to do is change your password for the email account. This should be done immediately. And when I say change your password, I don't mean from "MySuperSecretP@ssword1" to "MySuperSecretP@ssword2" as this is not an effective password change! Be sure to make significant changes to the password when going through this process or you will likely be hacked again.
Step 2 (Optional, but recommended): Notify your contacts
If your email has been compromised, it is always a good idea to create a new email and notify all of your contacts. Alert them that they may receive or have received an email you did not actually send. This email may contain malicious links and they should delete it upon receipt. This simple step can help prevent the spread of such attacks.
Step 3: Check the email rules in Outlook
In Outlook, check the rules to make sure there are no rules you did not create. Specifically, look for rules doing things like forwarding or copying emails to other email accounts.
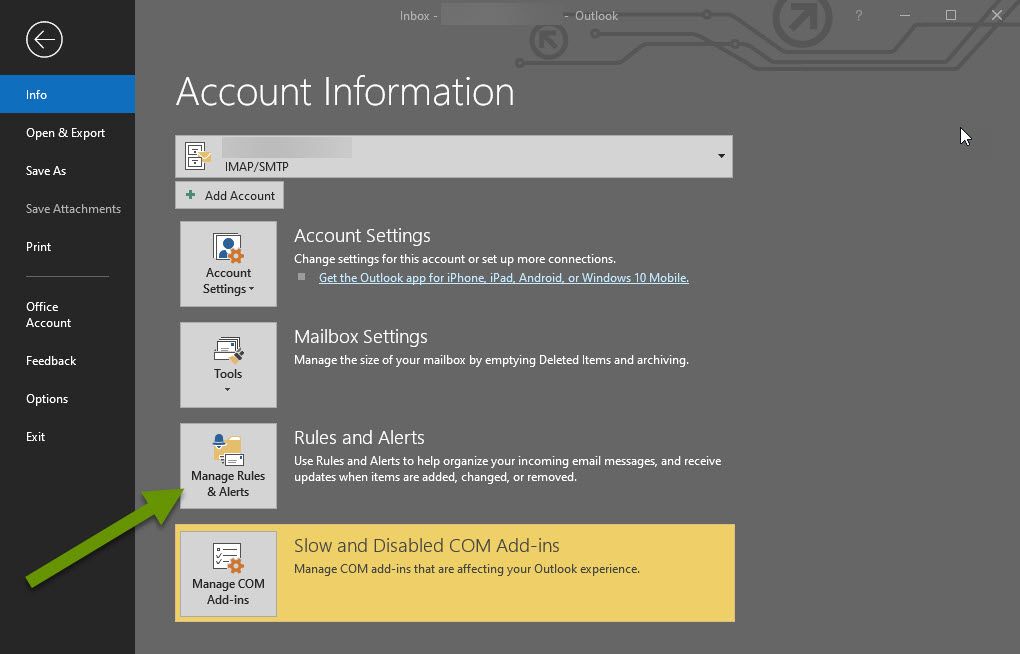
To access rules in Outlook:
- Click on File and select "Manage Rules & Alerts" in the right panel under Account Information.
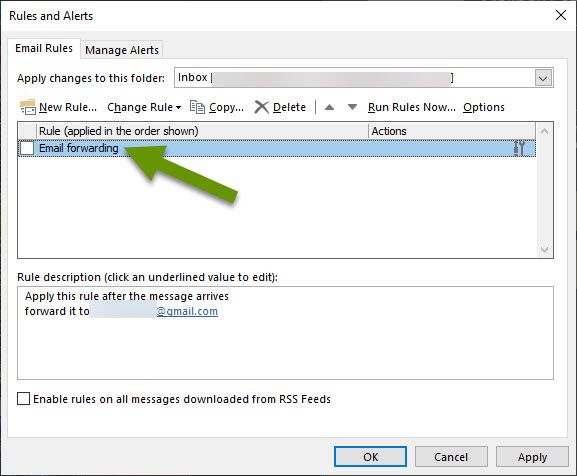
If you find a rule you do not recognize, click on it to view its description in the box below the rules. If this is not enough detail, click on "Change Rule" and select "Edit rule settings" to see exactly what the rules does. In the example above, I have appropriately named the rule I created, which is to forward email to another email address. However, someone hacking your email will likely name the rule something much less suspect so be diligent looking at rules. If you find any inappropriate rules or ones you did not create, click on them and then click the Delete button.
Keep in mind, when creating a rule like email forwarding, all existing emails in your Inbox can also be forwarded so it really pays off to be careful clicking links and preventing anyone from gaining unauthorized access to your email!
Step 4: Check the rules on Outlook.Office.com
After checking the rules in Outlook, it is important to log into webmail for the same email account at Outlook.Office.com. The purpose for this is to verify there are no email rules there that are not in Outlook. This is a step users often do not think of, but unfortunately, these rules do not always sync so if you leave this unchecked you might be surprised by someone still having access to your email.
To check the email rules for webmail:
- Open a web browser and go to https://outlook.office.com.
- Once logged in, click on the Settings cog at the top of the menu bar.
- In the Settings menu, click the "View all Outlook settings" link at the bottom.
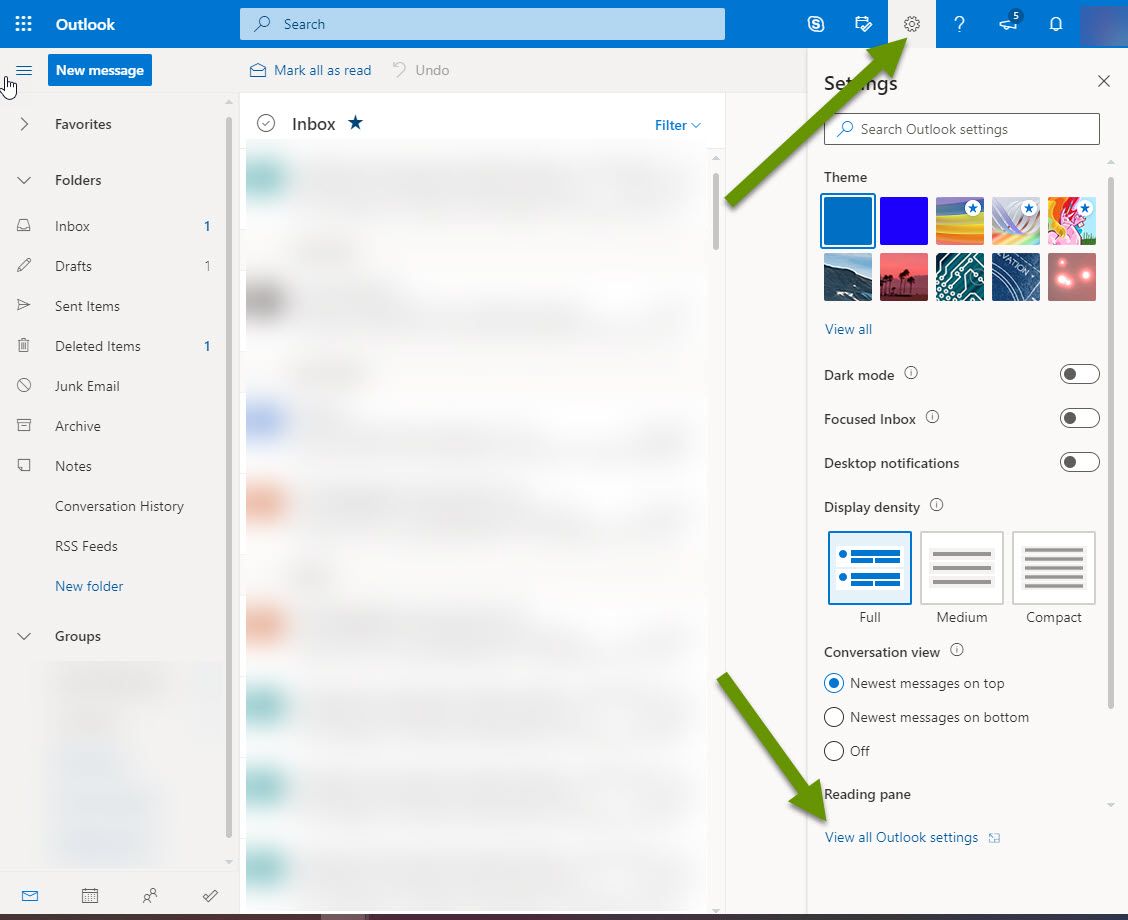
- In the Settings popup, click on the "Mail" heading in the left panel and then select "Rules" from the middle panel.
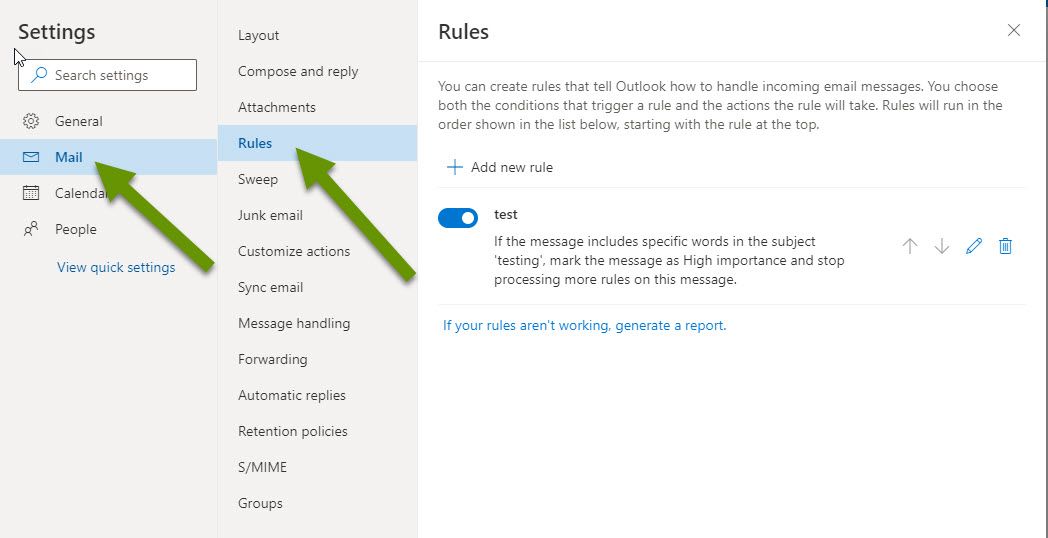
Check the existing rules the same way you did in Outlook and remove any rules that do not belong.
Once the steps above have been completed, you should not have any further email issues stemming from this attack. It is important to follow the steps as quickly as possible to get the person out of your account and block all access they had. Checking both places only after changing the password is the best way to regain control of your email account and prevent further unauthorized access.
As always, using caution to prevent unauthorized access to your email is far more efficient than trying to recover from being hacked!

