Security Update: Misspellings, the Latest Phishing Attack
Attacks against the security of our devices, and our data, are constantly evolving. The offenders of these attacks implement their schemes, track the success of them, tweak the attacks to be more successful and begin the cycle all over again. This is one reason why attacks are consistently changing. Other reasons have to do with changes in hardware and software and the vulnerabilities those changes can bring.
This post covers a recent and very popular phishing attack, which utilizes misspellings, to trick users and cause harm.
Security Update: Misspellings, the Latest Phishing Attack
A quick definition
A phishing attack is similar to other attacks in that the end goal for an offender is to gain unauthorized access to someone else's data. Phishing attacks come in the form of text messages, emails, or direct messaging. A big identifier for phishing attacks is that they employ social engineering to increase the odds of their success.
Social engineering consists of manipulating someone into giving information about themselves or their company that they should not give. It typically includes acquiring legitimate information which is then used to convince victims to give away private information, share access, or click links, etc. An example of a phishing attack would be receiving an email that you think is from your boss because the name is spelled correctly and it looks like her email, asking you to do something your boss might ask you to do, but the end result actually goes to the offender instead.
The latest type of phishing attack
Similar types of phishing attacks are often released in groups and may even focus on certain types of employees or businesses. A new form of phishing attack, purposefully incorporating misspellings, is quickly gaining popularity. There are several variants of this attack.
One version uses the incorrect spelling of a legitimate domain. As an example, a business name of Acme Baking Solutions might have a legitimate domain acmebakingsolutions.com. An offender could buy a similarly misspelled domain such as acmebackingsolutions.com or acmebakingsolution.com. The approach is to choose a common misspelling, swap similar letters or add/drop single letters, so people do not notice the mistake.
Buying domains that are easily misspelled is called typo-squatting. Offenders commonly target popular sites as their traffic volume makes them an ideal target. In other words, the more legitimate traffic they receive, the greater the likelihood there will be misspellings and the offenders will get traffic to their fake sites.
Once the offender has a similar domain, they can setup the new domain to appear to be the original domain, hoping to get users to click on links. Or they can create an entirely new site, also filled with malware. The main purpose is to get users to interact with the site so offenders can infect their machines with malware.
Another way misspellings are being used is with email addresses. So using the example above, an offender could find out the name of an actual employee at Acme Baking Solutions from their website, then send a strategically written email to an employee or client using the email from the incorrectly spelled domain. For example, using the email esmith@acmebakingsolution.com when there is an employee with the email address esmith@acmebakingsolutions.com, which might not be noticed by the recipient of the email.
Social engineering attacks are successful because we spend so much time sending information digitally AND we are often busy or so focused that we do not notice the subtle differences. We see the beginning of an email address we know and expect to get email from, and if the attacker does the right research, they can be quite convincing. If we do not recognize the danger, they might gain access to information they should not have or infect our devices for other purposes.
Real world examples
Barbara Corcoran, a famous investor and common entrepreneur on Shark Tank, was recently targeted with a phishing scam that cost her nearly $400,000. The scam targeted Barbara's bookkeeper, who received an email from what appeared to be Barbara's executive assistant, something not at all out of the ordinary which is key to the success of these attacks.
The email requested a wire transfer of nearly $400,000. Because of the amount, the bookkeeper replied and asked for supplemental information to verify the request was legitimate. Upon receiving clarification of the details, which included legitimate information and made this transfer seem proper, the bookkeeper wired the money. Unfortunately, it was not the executive assistant asking for the transfer.
So how did the sender of the email get away with appearing to be the executive assistant? They used the assistant's legitimate email minus a single letter and this went unnoticed by the bookkeeper.
The takeaway: While asking for more information is a good idea, it is only effective if you are sure you are communicating with the right person. Initiate your own contact before approving, clicking, or forwarding anything. Call, create a new email, use internal messaging systems, or whatever form of direct communication makes sense, to connect with the requestor. Whether they are requesting wire transfers, account or verification numbers, or passwords, be sure the person asking is valid before sending any private information.
If you are familiar with Rudy Giuliani you have probably heard of his infamous typos on Twitter. Anyone who uses Twitter has likely seen typos in tweets. The nature of the platform being short messages lends itself to being used on smart phones where it is more likely to accidentally have a typo compared to a standard keyboard.
Unfortunately, because Rudy is known for such mistakes, and has a large following, offenders have taken to using these mistakes against his followers. By buying up domain names he has mistyped, they are able to send people who click the links to their malware infested sites. A recent example of this happened in a tweet where Rudy accidentally put a space in a link to his website, causing users to be redirected to a completely different site.
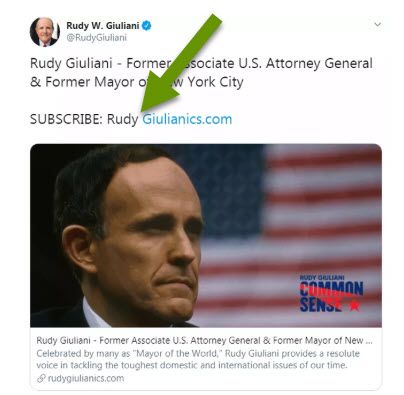
Users should have been sent to a page not found error if the misspelled domain was not in use.
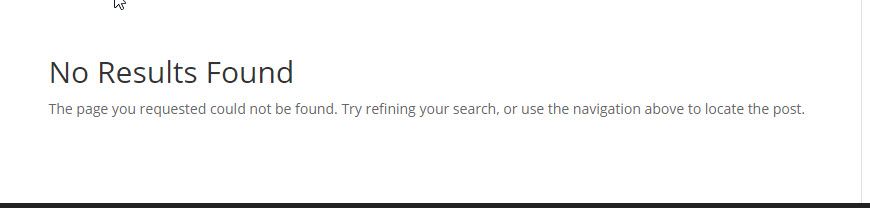
The takeaway: Whenever you click a link rather than going directly to it, be sure you check the link before clicking! This can be more difficult when the spelling is something you are less familiar with. In situations like this, try using a search engine you trust and look for legitimate results. It is always safer to seek out a link this way than click something someone else shares.
The newest type of phishing attack gaining popularity includes small misspellings of domains and email addresses. This can be done by omitting or adding a single letter, spelling the domain phonetically, as well as other small differences. Offenders buy up domains with these misspellings for the purpose of spreading malware that targets the security of our devices and data. The best protection is to go directly to domains, check the spelling of links before clicking, and to initiate contact with someone who emails you before giving away information.
As always, taking a little longer to be careful is often far less costly than the alternative!

