Security Update & How to Protect Remote Workers
Whenever there are major headlines in the news, hackers use them to attack innocent people in hopes of breaking their security. Unfortunately, the current pandemic is no exception to this phenomenon. Also, with the rise in remote workers, there are things you need to consider to protect yourself.
This post covers recent security scams related to COVID-19, as well as ways to protect your devices while working from home.
Security Update & How to Protect Remote Workers
The greater the popularity of an event or news story, the higher the likelihood someone is using that to try and hack your information. We saw this a few months back with the sudden and tragic death of Kobe Bryant. We are seeing it play out in multiple layers as a result of the pandemic. As the pandemic spreads and affects people differently, so do the attacks.

Formats of pandemic phishing attacks
Initial phishing attacks took advantage of people's curiosity. Increasing numbers of spam emails were sent using misinformation and especially fear. When we are fearful we often make quick decisions that are not in our best interest which is exactly what the hackers prey on. Some examples of what these phishing emails centered on were:
- General information about the virus and updates - often spoofing reputable sources of information like the WHO, CDC and others to build trust.
- Products and services claiming to help treat or prevent the virus - general misinformation increasing fear, confusion and panic.
Secondary attacks spoofed file sharing services once again, in an effort to get victims to click on links in emails. In both attacks, hackers use malicious links to send you to spoofed websites or to download malicious software. This allows them to capture user id's and passwords, to compromise your device and run unintended programs, or to access information you never authorized them to have.
Another version of this attack included sending emails with links to "a secure server". The purpose of using a secure server being misunderstood to get users to think clicking the link is safe. If you are not quite sure how sharing files with a secure server is used, please check out a recent post discussing how to upload tax documents to a secure server. This post has a good explanation of why and when to use a secure server, regardless of the type of documents used.
NOTE: A hyperlink claiming to point to a secure server does not mean that is where it actually goes or that the link is safe to click. A hyperlink can point to anything, regardless of what the text says. For more information about hyperlinks, please read the last section of our post from last year during consumer protection week which explains in detail how hyperlinks work and how they can be dangerous.
The latest form of attack adds an additional layer of fear by sending emails claiming the recipients have been exposed to COVID-19 through someone they have come into personal contact with. Of course, like all phishing attacks it pushes the reader to download a malicious attachment.
Spoofing a hospital in these attacks lends credibility which makes it even more dangerous. This particular tactic is especially disgusting, focusing on creating hysteria and encouraging the victims to head to the hospital, where resources are already limited and strained in many cases. Currently, the attached form, which is full of malicious macros, is only being detected by a handful of anti-malware programs.
What is likely to be the next form of attack, based on information from the FBI's Internet Crime Complaint Center or IC3, is phishing emails referencing stimulus monies coming from the federal government. Knowing monies are being released for citizens lets hackers use this as an opportunity to reach out to individuals in hopes of getting private information requested to "send them their funds."
Check out this article by KnowBe4 for more information about the pandemic phishing attacks and the timelines.
The Takeaway: Hackers are looking to take advantage of the fear created by the pandemic. If you want to protect your documents, your privacy and maintain the security of your documents, you must be hyper-diligent when opening emails, going to unknown websites, and clicking links in emails and on websites. Also, keep in mind that hospitals should not be sending this kind of test result through email. They will either call you directly or send you an email to log into their system and access messages securely there.
How to protect remote workers (including you!)
In addition to the protections listed above in the takeaway, there are two main things you need to do to protect remote workers, including yourself. These include: having endpoint protection actively running on your devices, and have cloud-based backups for all local stored documents.
Many people newly working from home are working on devices they just purchased or were given to them in haste when the self-quarantine orders came down. This means these devices are less likely to have endpoint protection or backups in place. IT staff may not have had time to finish prepping the device or perhaps you bought it and have had far too many other things to worry about since getting it. Either way, investing in both of these will save you far more than their cost.
There are several brands of endpoint protection, but there are two main things you should look for, including:
- Real-time protection, meaning it is actively running all the time AND
- Protection from viruses, worms, trojans and other malware INCLUDING Ransomware protection.
NOTE: If your endpoint protection does not protect against Ransomware, having cloud-based backups is an absolute necessity to protect your local documents.
When it comes to cloud backups it is first important to understand the differences between cloud storage and cloud backups.
Cloud storage typically includes only a single version of all of your files and perhaps a set amount of time for deleted and modified files to sit in a recycle bin. Many services, like OneDrive, will sync files across multiple devices if logged into the account. However, easily accessing previous versions of files is less common. Additionally, files are updated or uploaded to cloud storage when files are added to or saved in the program folder.
Cloud backups run automatically based on a schedule set by the user. A complete snapshot of data from any backup date is available for recovery as long as it falls within the data retention window. This means you can restore a complete set of data back to a date BEFORE something happened and recover all the files to the state they were in at that date and time. The data retention window can be set to any amount of time; our solution defaults to 90 days for example.
There are also several brands of cloud-backup solutions, but be sure to look for the following:
- Data retention that you control. It is common for one-size-fits-all plans to include less controls, including not allowing the user to determine how long file versions are kept.
- Audit reports. These are especially important for businesses and are required for any business subject to HIPAA, FINRA or SEC restrictions. There are many things audits can log, so be sure you understand what is audited. At the very least, it should include account failures and logins, users downloading files, and adding or modifying existing backup jobs.
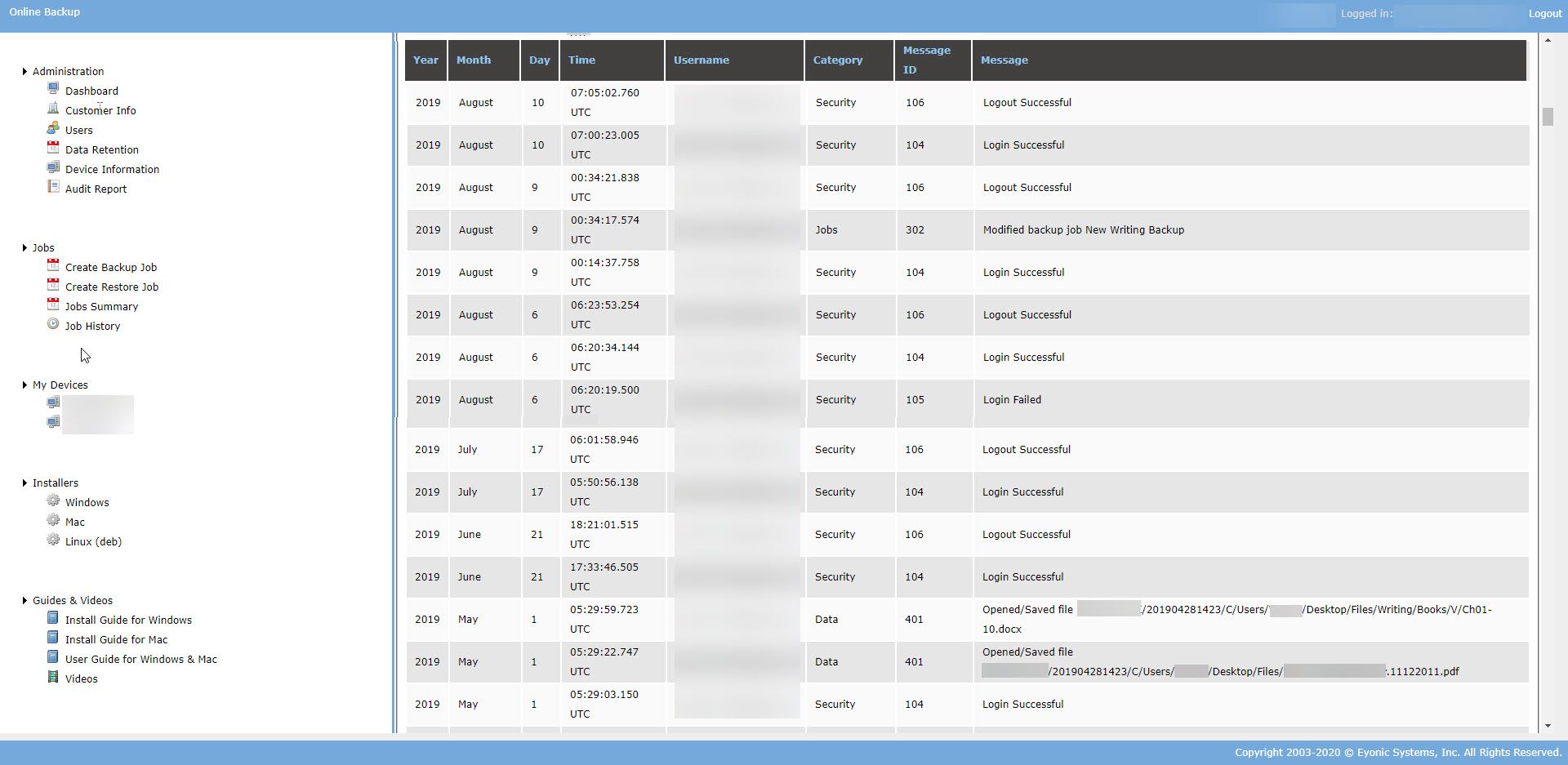
While more and more people are working from home to stay safe during this pandemic, in other ways they are at greater risk. Hackers are taking advantage of the fear and stress brought on by the pandemic in hopes of getting users to open emails and click on malicious links. Additionally, using devices without endpoint protection and backups puts you at greater risk. Be sure to protect yourself even though it may seem like a low priority now, as it will be much more costly if you do not.
As always, being aware helps us know how to protect ourselves and plan ahead which always saves time, money and frustration when it comes to technology!

