Security Updates: Clubhouse/Facebook Breach and the Likeliest Malware Threat Source
New security threats are introduced, found and patched nearly every day, not all in the same day of course! Some threats are directed at you as an individual, while others are directed at companies you and others do business with. The larger the company, as well as the greater the amount of data they have about you, the bigger target that company can be.
For example, the healthcare industry is often targeted because these institutions have so much information about their clients. Banks and big companies like Amazon are also often targets because of the sheer amount of people using their services, which means hackers are more likely to be targeting an actual customer when they send their phishing campaigns out.
This post discusses the recent Clubhouse/Facebook breach and where nearly half of all malware installations come from.
Security Updates: Clubhouse/Facebook Breach and the Likeliest Malware Threat Source
When a company you have created an account with suffers a data breach, there is nothing you could have done to prevent this threat to your data. However, there is something you can do that will help protect you every time you create an account with a different company - use different credentials. Using different credentials for each account protects every other account you have when one is accessed by an unauthorized user. This is especially true of your email user id and credentials as it is often how you recover other accounts. Check out this previous post for why using unique email credentials are absolutely critical in protecting your data and accounts.
Clubhouse/Facebook breach
Last week a data breach that affected 3.8 billion Clubhouse and Facebook users was reported. The database in question was reportedly being held for auction at an asking price of $100,000. The data includes names, phone numbers and addresses of those people affected. Unfortunately, because of the way Clubhouse required users to share data, your information could have been breached even if you were not a Clubhouse user.
The actual data breach occurred in early September on Clubhouse servers, but Clubhouse members were required to share their entire contact list with the app in order to be able to use it. This meant their contact list could have synced with Clubhouse and included all of their contact's phone numbers. How Facebook users' ID's also ended up in the database has not yet been made clear, but some suspect the information in this hack was compiled with prior Facebook hacks.
The takeaway - There is nothing you could have done to prevent your account information from being breached if you used the Clubhouse app, or if you know someone who did and were in their contacts list. However, it is absolutely your choice whether or not you use an app that requires you to share your entire contact list just to use it. If more people said no to these kinds of privacy violations, less of us would be at risk.
This is also a good reminder that while you can be as careful as possible, anyone who has some of your information can still put you at risk. Almost everyone has received a phishing email from someone they know because their email was compromised and emails were sent to everyone in their contact list. Apps requiring users to share their contact lists are putting more people at risk than is necessary and avoiding them will help protect you and the people you know.
Lastly, if you have used Clubhouse, be sure to change your credentials and update them anywhere else the same credentials were used (which they shouldn't be!).
Where 43% of malware infections originate from
With more people working from home or remote office locations without centralized servers, file sharing by sending emails has become far more common. As a result, attacks that can exploit this change in process have gone up exponentially.
According to recent research, based on the July 2021 Netskope Threat Lab Cloud and Threat Report, malicious office documents have increased to 43% of malware installations. Office documents include files from programs and applications you would expect, like Microsoft, but also Google Docs and PDF documents. To realize how dramatic a shift this represents, it is important to know that a year ago documents accounted for only 14% of malware installations.
Documents have hostile macros embedded in them before they are sent to unsuspecting recipients. What makes these attacks so successful is that they often avoid detection by anti-malware applications because they are seen as a simple document. Additionally, the documents are often sent in such a way that they appear to be coming from a reliable or known source.
The takeaway: It always pays to be careful opening documents sent to you in email - even if you know the sender and it looks to have legitimately come from their email account. Where possible, check that the email account is what you would expect based on the sender's name, verify the user did indeed send you the document, preview the file (like in Outlook) which by default should prevent macros from running or prompt you to run them, and always have endpoint protection and offsite backups installed and running on your device.
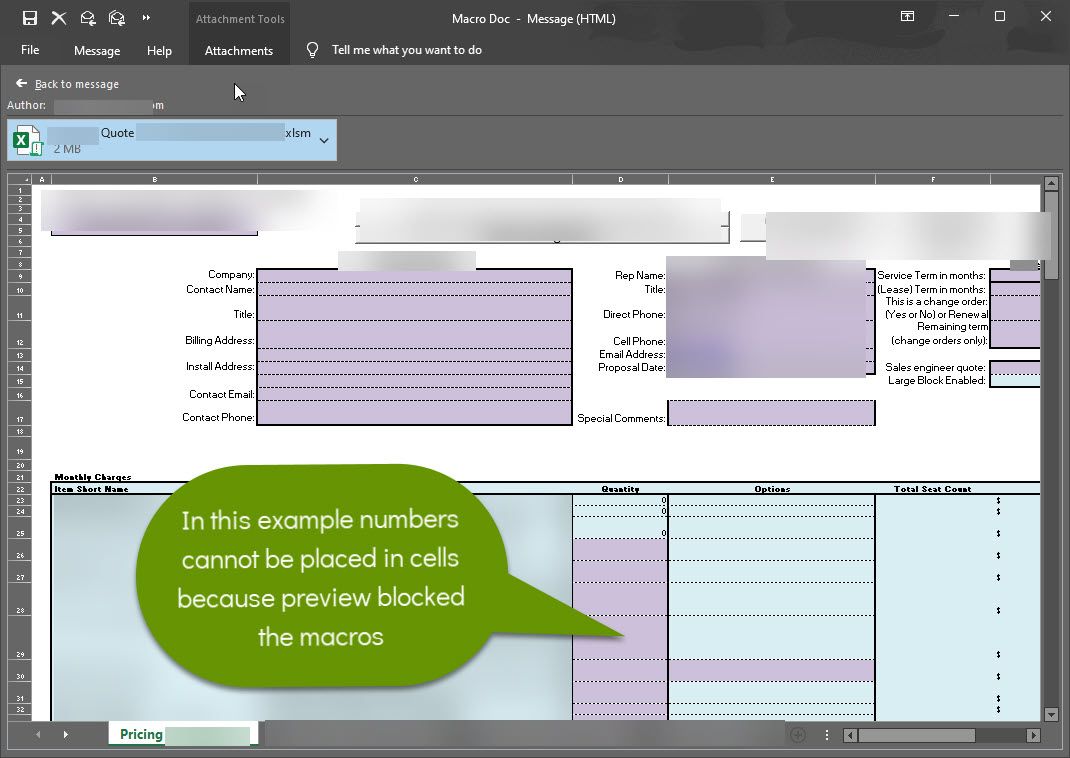
Again, the fewer items you open from other people, the safer you will remain. Accessing documents directly from a file server, rather than being sent via email, is also safer. If possible, exchange documents via file sharing services so users are not expecting documents to come to them in email and do not open maliciously sent emails with infected documents.
Security threats are never going to go away. What is important is being as aware as you can be of the types of threats going on, sharing information with others to help protect them, using caution opening email from unknown senders, and most especially, avoiding clicking on links or downloading files sent via email. Wherever possible, go to the source instead.
As always, the more aware you are and the more cautious you are, the safer your data and privacy will remain!

