Security Round Up: Windows Vulnerabilities, Ransomware and More
We are only a few weeks into the new year and already there are new security attacks and repeat offenders in the news. Patch Tuesday was a really big deal for Microsoft this month and you will want to reboot your computer sooner rather than later to apply those changes. There have also been ransomware attacks and numbers about these attacks released from a study. Lastly, we discuss a malicious O365 app that can gain unauthorized access to your documents and circumvent password changes.
This post covers these threats in detail, what you need to know about them and what you can do to protect yourself.
Security Round Up: Windows Vulnerabilities, Ransomware and More
Microsoft flaw may allow malware to bypass end point protection
Multiple news sources this week reported several high impact security flaws within Microsoft Windows operating systems. One flaw, called a CryptoAPI spoofing vulnerability, affects:
- All 32- and 64-bit Windows 10 operating systems
- Server 2016 devices and
- Server 2019 devices
This vulnerability affects proper certificate validation, allowing it to be bypassed. What makes this so scary is that the malicious software could work around endpoint protection software because of the certificate issue. Lastly, data can be injected into user connections without them ever knowing it which puts users at great risk.
The second flaw, a Windows remote desktop protocol vulnerability, affects Windows Servers running 2012 or newer, as well as devices running Windows 7 and newer. This vulnerability allows remote code to be executed without user interaction or requiring authentication. However, the flaw first requires a user to connect to a malicious server.
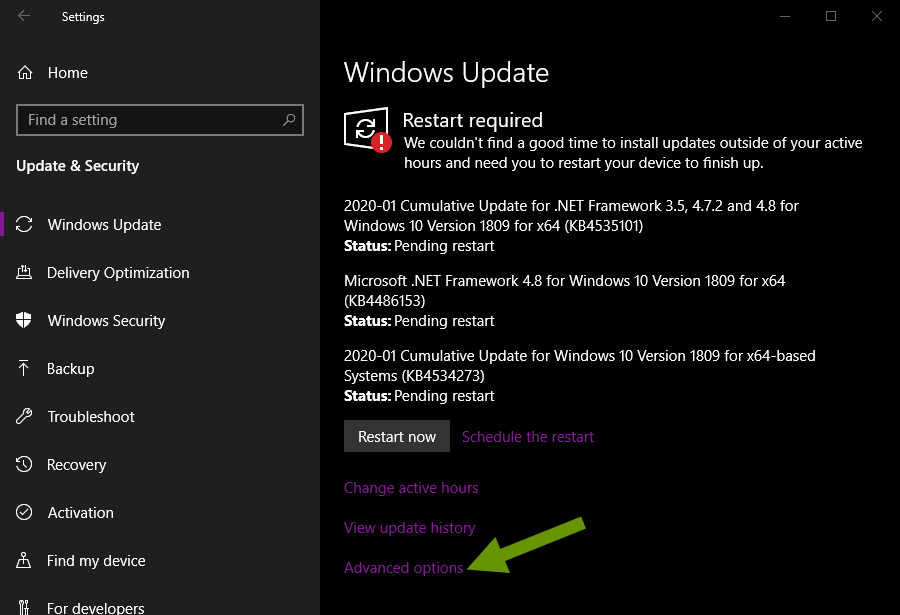
Moving forward: Both vulnerabilities were addressed earlier this week on patch Tuesday. Users should receive these updates automatically unless they have suspended updates. Be sure to reboot your computer if you have reboots set to prompt rather than being done automatically. To check your update settings, open Settings, click "Update & Security" and click on "Advanced options" under the current Windows update information.
An example of pending updates requiring a reboot to be implemented is shown below:
Results of a ransomware attack plus the latest attack target
Ransomware consists of an attack that, if successful, infects the victim's computer and encrypts their files. Ransomware infects a system by tricking a victim into clicking a malicious link. One of the things that makes it so dangerous is that ransomware also encrypts any physically attached local drives, like USB drives, as well as any locally mapped drives connected to storage devices and servers.
Most recently, schools have become a common ransomware target. A recent report by Armor found 72 school districts in the United States publicly reported being a victim of ransomware since January 2019. Eleven of these school districts reported since October, showing how attacks on schools are increasing. The report went on to state that up to 1,039 schools may have been impacted nationwide.
A company in Arkansas, who fell victim to a ransomware attack, recently let 300 employees go. The Heritage Company, who paid the ransom to decrypt their business files, struggled to recover after the attack wreaked havoc on their business. Even though they paid the ransom, it was not enough for the company to recover from the attack and go back to business as usual.
Paying the ransom to decrypt your files, which is often costly, is only part of the process. An attack can have any of the following impacts and more:
- Costly employee down time
- Costly equipment replacement and/or technical support
- Loss of business revenue
- Loss of business reputation
- Loss of business data even if the ransom is paid
Recovering from a ransomware is a process that includes:
- Preventing the malware from spreading to other machines on your network, if applicable.
- Removing the infection from any infected machines.
- Recovering all encrypted files and restoring file access to end users
This list is deceptively short. Each of these processes can take hours, days or weeks to overcome, if at all. One of the most important steps is recovering your data. If you do not have a current unaffected backup of all of your files, then your only choice is to recreate the files or pay the ransom for the decryption key. Keep in mind, paying the ransom is no guarantee that you will receive the correct decryption key.
Moving Forward: As with any ransomware attack, the best possible prevention is using caution when clicking links, especially those sent in emails. Second, always keep a viable and current backup of your important files. The quicker you can begin a file restore process after any type of attack, the greater you reduce the risk to your business.
Malicious O365 app allows access to data
While many security attacks focus on stealing credentials to gain unauthorized access to people's data, a recent attack utilizes a malicious app. The attack requires the victim to click on a malicious link which then requests the victim's O365 credentials. Once these are entered, the attacker gains access to the victim's mailbox, contacts and files stored in OneDrive.
So why go to the trouble of building an app instead of using a spoofed logon page? The answer lies in how differently apps and web-based connections handle logins. With this app, even if the victim learns their credentials have been compromised, changing their password does not disconnect the app. By contrast, changing their password would work with traditional attacks.
Moving forward: This attack still relies on the end user to click a malicious link. Your best protection is to question the authenticity of each email, every link and certainly anything that uses pressure in hopes of getting you to make a quick decision. If you are a victim of this type of attack, you can still preserve your account. Before changing your credentials, be sure to disconnect the previously allowed app to deny its access.
New security attacks will continue to be released in hopes of taking advantage of hardware and software vulnerabilities. More importantly, many forms of attacks require user interaction, typically in the form of clicking a malicious link. The best way you can protect yourself is to be diligent, question the source of the information, and stay in the loop about current threats as much as possible.
As always, keeping a level head and using caution when clicking links in web pages and in emails is critical to staying safe!

