Security Round Up: Ransomware Victim Foxconn & a New Browser Hijacker
The end of the year often feels very hectic for people. If you own a business, you are busy trying to wrap projects up before the end of the year, get ready for tax season and finish mapping out the next year. If you are an employee, you are wrapping up projects and managing your home/work life balance. Not to mention planning for the holidays which has only gotten more challenging being in the middle of a pandemic.
Unfortunately, the busyness created during this time of year proves to be the best timing for hackers to attempt to steal your data or otherwise violate your privacy and security. Why? For the reasons I already stated. People are busy, possibly distracted and probably overwhelmed. This increases the likelihood that you will make a quick decision and accidentally click a bad link or install the wrong software.
This week we discuss two major security breaches including ransomware and a new browser hijacker.
Security Round Up: Ransomware Victim Foxconn & a New Browser Hijacker
Foxconn ransomware attack
Just over a week ago, Foxconn, an electronics manufacturer, suffered a ransomware attack. This attack resulted in stolen company documents that were leaked, encrypted files and deleted servers. The demand Foxconn received from the hackers to acquire the decryption key for their data? A payment of $34.7 million in Bitcoin.

You might not have ever heard of Foxconn, but they happen to be the parent company of both Belkin and Sharp Corporation, both of which you most likely are familiar with. A ransomware hit is devastating to any business, and in this case to operations and manufacturing. Without access to business files it can be impossible to track inventory, place or accept orders, package shipments, accept payments and much more!
Ransomware is extremely effective because it only needs to successfully infect one device on your network. From there it spreads by connecting to all locally attached drives as well as all mapped drives. Mapped drives typically point to storage devices or servers, where a great deal of business data is likely housed. Once connected, ransomware encrypts all the data on these devices as well.
This is why backing up a device to an external USB/flash drive is not as reliable as a cloud-based backup service. The only way an external USB drive works as a backup system is if you disconnect them from the device backed up after each back up job, run regular backups to them, and often rotate them to an offsite location.
The takeaway: Ransomware if effective and often devastating enough to a business for them to pay the ransom. As a result, it is not going away any time soon. Every year businesses of all sizes in all sorts of industries have fallen victim to ransomware attacks. The thing they have in common? Recovery, if possible at all, is EXPENSIVE! Whether you are a small shop or a large corporation, replacing equipment, possibly paying a ransom (please don't), reinstalling software applications and other plugins, repairing your reputation, and possibly most costly of all - employee downtime, can run you out of business.
A cloud-based backup service costs much less than recovering from a ransomware attack, provides peace of mind to your business and your customers, protects your customers and preserves your reputation. If you have not already invested in a solution, take the time to do so!
New browser hijacker
A shady new search browser was recently released and is gaining popularity. The offending browser is called WebNavigator. It is typically found through advertisements that redirect you to browser extensions and other ads. Once installed, it works much like other search extensions that redirect your searches to a third party before passing them on. Their sole purpose is to make money from advertisers based on your clicks.
WebNavigator is a Chromium-based web browser, like the new version of Microsoft's Edge and Google Chrome. Chromium is also the default browser for Linux-based systems. WebNavigator is being installed by users who likely have no idea what they are installing, only that WebNavigator claims it will simply your web browsing experience.
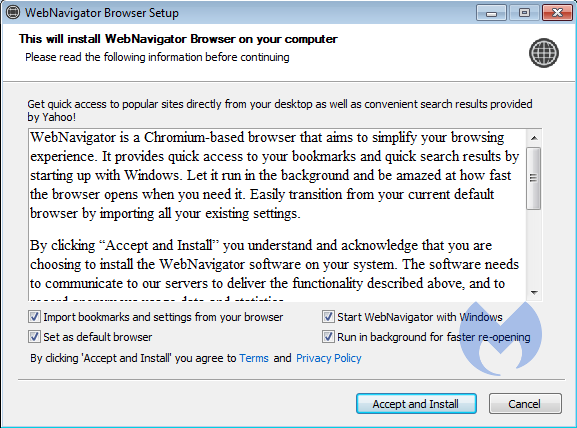
If you have endpoint protection software like Sentinel One or Malwarebytes installed on your device, WebNavigator should be blocked before you can install it as they recognize parts of the software behaves like malware.
One clue that you may have accidentally installed the WebNavigator software is the integration of images in search results for ads that were not there before. If you suspect you have installed this browser, you can verify by checking your task manager to see if its services are running. If you accidentally installed this extension, remove it and be sure to run a system check on your device to ensure no remnants were left behind.
For more about WebNavigator and how it operates, read this article published by Malwarebytes.
The takeaway: It is always easier to not install bad software on your device than it is to remove and recover from the malware later. Having endpoint protection software is key as it can automatically block known malware as well as warn you about suspected malware.
Attacks like ransomware, browser hijacking, and all other nefarious ways to gain access to your files or breach your security often rise during the holiday season. People are busier, more distracted, spend more money making purchases online, feel rushed, and therefore are more likely to make a quick decision they will later regret.
To protect yourself, be especially careful of applications and extensions that seem too good to be true or that you did not specifically pursue. Lastly, make sure you have an offsite-based backup system in place and have up-to-date endpoint protection on every device!
As always, attacks will continue, having backups and endpoint protection keeps you from being low hanging fruit to the bad guys!

