Security Round Up: 21M Records Exposed, a SonicWall Vulnerability & Windows Malware
As with every month, there have been several new threats to our data and privacy. Most recently, there was a data dump that included personal information on 21 million people, a vulnerability in some SonicWall firewalls, and malware directed at Windows systems.
This post discusses what happened, what you need to know, and what you can do if you were affected by any of these.
Security Round Up: 21M Records Exposed, a SonicWall Vulnerability & Windows Malware
These most recent breaches affect a very large population, making it more likely you have fallen victim to one of the attacks. The more familiar you are with the types of attacks occurring, the better you can protect yourself and your data.
21 Million records exposed
Last week a 10GB database consisting of 21 million user records was exposed on Telegram, a secure messaging app. The database had previously been for sale on the dark web, but is now available for free. The records include user data from three common VPN providers. Some of the personal information included in the breach are:
- Full names
- Usernames
- Country
- Email addresses
- Billing details
- Randomly generated password strings
What you need to know: The three VPN providers affected are: SuperVPN, GeckoVPN, and ChatVPN. Additionally, 99.5% of the email addresses exposed in the breach are Gmail accounts.
What you can do: If you have a VPN account with any of these vendors, you should change your password as soon as possible. Additionally, it is always important to keep an eye on changes to your credit, including credit history, to help prevent and/or catch potential identity theft before it can adversely affect you. Regularly checking your credit history can also help catch mistakes before you need to use your credit for something like qualifying for a large purchase, e.g., a mortgage loan.
SonicWall vulnerability
SonicWall recently urged customers to upgrade some of their firewalls to the latest software which includes a patch addressing several vulnerabilities listed as high-risk. As reported, the vulnerabilites only affect SonicWall's Secure Mobile Access (SMA) 1000 series products. These are often used by businesses to provide secure remote access to resources, regardless of whether those resources are cloud-based, on-prem, or a hybrid of both.
What you need to know: According to SonicWall, the vulnerability with the highest risk could allow attackers to bypass authentication, meaning they could potentially gain access to internal resources. Luckily, this vulnerability has not been detected in the wild so far, but it does pose a very serious risk.
What you can do: If you have a SonicWall SMA 1000 series device on any of your networks, make sure you run all available updates as soon as possible. As with every device that has software, updates often include important security patches. Additionally, many of these require the user to initiate installation of updates. Where possible, set security updates to install automatically.
Windows malware
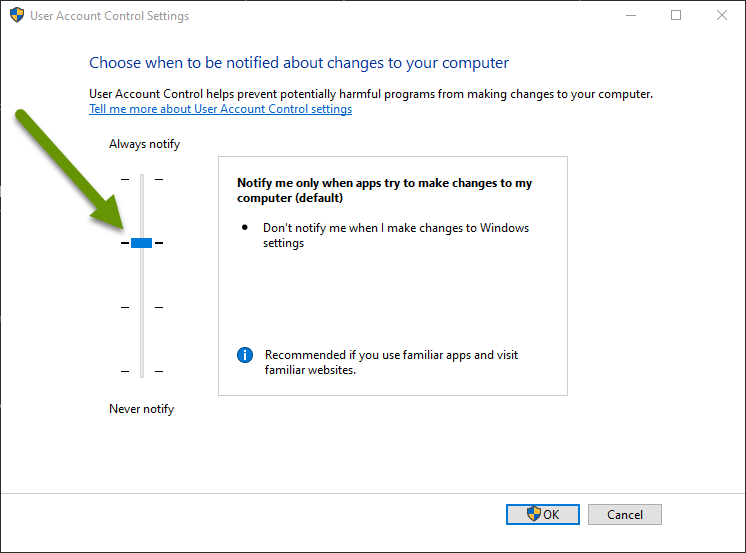
Recently, a malware being spread to Windows devices via USB drives was exposed. This malware has worm capabilities and uses the Windows built-in command prompt app to launch a malicious file stored on the infected USB drive. This is a complex attack that first bypasses User Account Control (UAC) settings before moving on to execute malicious files. UAC is the security application that prompts you to confirm you want to allow an application to make changes to your device when you attempt to install software.
NOTE: UAC has several different security level settings, including being set to "Never notify". It is not recommended to turn the setting down this low as these notifications can sometimes prevent programs from being allowed to install when you might otherwise have been unaware that was what was happening. To access your UAC settings, simply search for UAC and select "Change User Account Control settings".
What you need to know: This malware is part of a cluster of malware originally identified in September of 2021. There is still much that is not known about how this malware operates beyond knowing it is currently spreading via infected USB drives.
What you can do: It is always important to be EXTREMELY careful plugging USB drives into your devices. If you are unsure of where the USB drive came from, or who may have had access to it since you last used it, do not plug it into any device with personal information. This includes devices you use to access bank accounts, store passwords in web browsers, etc.
If you find a USB drive, you absolutely do not want to plug it into any device you own. Infected USB drives are often left in parking lots and busy office buildings in addition to being mixed in with regular USB drives at conferences in hopes of capitalizing on unsuspecting conference attendees.
New threats are constantly being released and it is nearly impossible to be aware of every threat. However, the more you are aware of, the better you will understand the methods being used, what puts you most at risk, and what you can do to better protect yourself. All of these make you a smaller target to attackers. Most recently, millions of records were exposed on Telegram, some SonicWall devices need to be patched, and always be careful inserting a USB drive into your devices as they may carry malware.
As always, the more careful you are and the more you question something before taking action, the better off you will be.

