Current Security Threats: Windows, Google Chrome, Cryptocurrency & More
The last few weeks have been rife with security threats and vulnerabilities. In this post we discuss some of the most current threats and vulnerabilities, including some that affect the Windows operating system, the Google Chrome browser, a malicious cryptocurrency application and more. Regardless of which piece you find most interesting, be sure this is your takeaway:
Run the available updates on whatever devices you are using! Keeping devices up-to-date provides extra protection and decreases your suitability for targeted attacks.
Current Security Threats: Windows, Google Chrome, Cryptocurrency & More
This post discusses attacks related to the:
- Windows 32-bit kernel
- Google Chrome browser
- AppleJeus and cryptocurrency
- Florida water treatment facility
Windows 32-bit kernel flaw
A recent vulnerability was found in the Windows 32-bit kernel that affects several versions of the Windows Server and Windows 10 operating systems. This flaw has been exploited in the wild and is extremely dangerous. When exploited, it allows an attacker to log into the system and execute code that gives them system privileges.
There are several different levels of privileges for an operating system. When you log in as a user and do something like open a web browser or print, these applications are opened using your user privileges. Other tasks, like running Windows updates, requires system level privileges. System privileges allow changes to the operating system, the registry and other critical areas. Being able to operate at the system level is very dangerous because it is the highest level of privileges possible.
What to do: Microsoft has already released a patch for this vulnerability so all you need to do is install it. If you are set up for automatic updates, you likely don't need to do anything. However, it is always a good idea to check and see if a reboot is required to finish the update. An update that requires a reboot has NOT finished installing and will NOT protect your device!
There are two places to find out if updates are pending and require a reboot. The first place is in the right-most portion of your taskbar.

The second place can be found by opening Settings and clicking on "Update & Security". This will show if a restart is required.
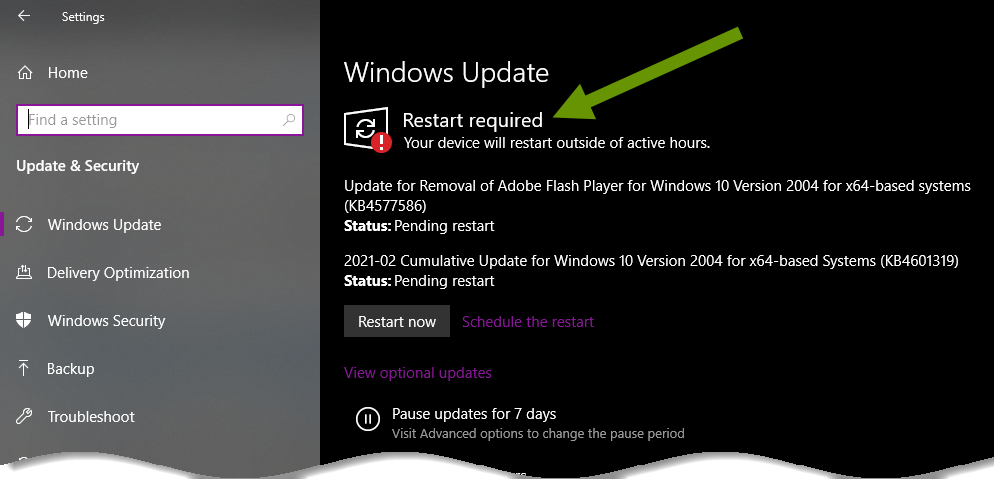
NOTE: It is better to be proactive with these reboots as they can take 15 minutes to a few hours to finish. Run them when you are able to walk away from your computer for a while so you aren't surprised by them later when you have something important or timely to do.
Google Chrome browser
A vulnerability in the Google Chrome web browser was recently exposed. This vulnerability applies to any operating system running the Chrome browser, meaning Windows, Mac and Linux devices can be affected.
At this time, there is very little information about this vulnerability other than it has been exploited in the wild. This is why Google is waiting until most users have patched the browser before releasing information that could put unpatched users at greater risk.
What to do: Google has already released a patch to address this vulnerability. Chrome should update automatically, but users will need to close and restart Chrome to finish the update. This means closing every instance of Chrome at one time to effectively update the browser. If your browser has the word "Update" in the upper right corner where the menu dots usually are, you should restart your browser as soon as possible.
AppleJeus & cryptocurrency
The Cybersecurity and Infrastructure Security Agency (CISA), FBI and the Treasury have been working on a joint advisory surrounding a threat by North Korea on cryptocurrency. This threat targets both companies and individuals, and possibly more alarming, cryptocurrency exchanges.
This threat works by sharing cryptocurrency trading applications that have been infected with malware which lead to the ability of hackers to steal cryptocurrency. The cybersecurity community has labeled this activity AppleJeus, which has existed since 2018 and has targeted 30+ countries in the last year.
AppleJeus applications have been found on both Windows and Mac devices. Part of why this attack has been so effective is that these applications come from a website that looks legitimate and users are encouraged to download the malware infested applications.
What to do: Be very careful about where you download cryptocurrency applications. Where possible, wait until this threat lessens to do so. There is much more to this story, if you think you may have been impacted, read this article for more information about AppleJeus, where to look for an infection and how to move forward.
A Florida water treatment facility
A water treatment facility in Florida was compromised by a cyber attack in early February. Unauthorized access to the supervisory control and data acquisition (SCADA) system allowed the manipulation of the amount of lye being added to the water during treatment in the software application.
Luckily, in this case, the water treatment process was unaffected due to the diligence of onsite personnel who noticed the change, knew something was wrong and went about fixing the issue. This attack utilized desktop sharing software, which can be extremely helpful in supporting devices remotely, but also introduces risks. This occurrence is a reminder of how delicate the management of some of our most necessary systems are, and how people's understanding of those systems makes a big difference.
What to do: For the average person, there is nothing you can do about attacks of this nature. If you work at a facility like this, it is important to stay alert and always question when something changes unexpectedly. Additionally, if you discover a threat in your normal life, expose the threat in a way that can help others. Share what information you can with the company that was a target, warn your friends, share information anywhere that might help spread the word and stop the attack, just be sure not to share any confidential or private information in the process!
Security threats are released and discovered every day. It is nearly impossible to avoid them all or buffer against every attack. Some attacks can be avoided by your actions while others are things you could do nothing to prevent. Many of the current threats shared above can be managed by applying available security updates so be sure to do them as soon as you can!
As always, taking the time to apply security updates is well worth the investment!

