3 Things You Need to Do if You Think Your Email was Hacked
Finding out your email account may have been hacked is something everyone can agree they never want to happen. If someone gets ahold of your email account they can cause all kinds of problems. Any amount the following things that can happen:
- Emails can be sent on your behalf - this includes malicious emails, emails to spoofed websites and emails requesting payments.
- Email rules can be set up - this can include automatically forwarding emails to an external email and much more.
- Resetting accounts - accounts using the email can easily be found by looking at your existing email, and passwords to log into these external accounts can be reset.
- Much more!
Luckily, there are a series of three things you need to do if you think your email was hacked. Keep in mind, efficiency is important!
3 Things You Need to Do if You Think Your Email was Hacked
Step 1 - Change your password
The most important thing you need to do is change the password associated with this email account. Depending upon how the hacker got your password, this may or may not prevent them from continuing to access your email. If you think your device has been compromised with some form of malware, be sure to use a different device to reset your password.
This helps prevent the password from being captured yet again from certain types of malware and keystroke loggers. Also, you will want to run a full malware scan against the machine in question. Once the password has been successfully changed and you can access the email account, move on to the next step.
Step 2 - Check sent messages
A common misuse of an email account is to send emails to the victim's contact list. The purpose of this is to garner more information, payments, or spread the attack. Emails sent like this might include links to malicious software, links to spoofed sites to garner additional user credentials, or even to collect payments. Money asks are a very common scam that work in tandem with compromised email accounts.
Some payment requests come in the form of links referencing invoice numbers, job sites or other valid information they gathered from poking through your existing emails. Others requests are for gift cards. Gift cards are popular because they are prepaid and easy to use without being tracked.
If you find messages in your Sent items folder that you did not send, contact the recipients immediately. Use some other form of communication like calling, messaging, or even having someone else in your office email them whenever possible. Explain what happened and make sure they know you did not send the emails in question and encourage them to delete them right away.
If they have already opened the email or clicked a link, they should follow these same steps to further prevent the spread and effectiveness of the hack.
Step 3 - Notify your contacts
Even if you do not have emails in your Sent items folder that you did not send, you should notify your contacts of the attack. A more sophisticated hacker will send emails on your behalf, then remove them from the Sent items and Deleted items folders so that no record remains of the emails.
The fastest way to communicate with everyone in your contact list is by sending yet another email. Use the BCC feature just in case someone interacted with a harmful email to prevent further spread. Be sure to inform everyone not to open any suspicious emails they received from you. Explain that these emails should be deleted immediately. Encourage them to contact you directly if they have questions about an email. Lastly, provide them with an alternative way to contact you.
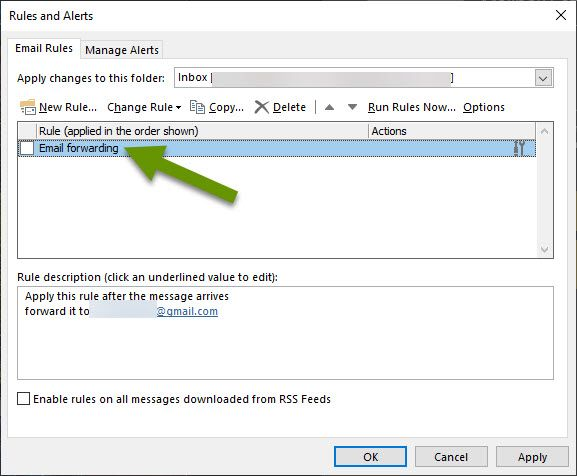
Optional Step - Check email rules
If you use Outlook or any other email that allows email rules, check to be sure rules were not created by the hacker. Types of rules include forwarding copies of all new or existing emails to a separate, external email, automatically moving emails into specific folders, and much more. Rules can have a great impact on email so it is very important to be sure rules were not added without your knowledge.
To check the rules in the Outlook app, click File, then select "Rules and Alerts" in the right pane.
Alternate issue - Similar email
If someone starts sending emails as if they were you from an email that is similar in nature, but different than yours, there is not much you can do to stop them. For instance, if you're using a free internet email like Outlook.com, Gmail, Yahoo, Zoho or any other email like this, you are creating a certain level of risk if you own a business. For individuals, this is typically not an issue.
The risk is introduced because typically when someone creates a free email account for their business, they only do so with one or perhaps two of the available providers. This makes sense, providers change often, and most people do not want to manage six to seven email accounts, even with email forwarding.
Unfortunately, what makes it easy for you to get these free email accounts also makes it easy for someone else to do the same thing. Once you have an established email, someone else could create the same username at a different email provider or create a very similar username with a few character differences at the same email provider. Once they have these email accounts, they can start sending emails pretending to be you.
If any of your contacts report getting suspicious emails from you, verify the emails they received actually did come from your email address before taking the steps above. Though it never hurts to change a password, it is good to know exactly what you are dealing with. If it happens to be a different, but similar, email account, warn your clients of the nefarious email.
If you think your email has been hacked, immediately change your password. It is also important to follow up with your contacts to notify them and check for emails in your Sent items that you did not send. Check for inappropriate email rules and remove any that you did not create. If people contact you stating they are receiving suspicious emails from you, check to be sure those emails are indeed from your email account.
As always, the more we communicate with others about things that happened to us, the better we are going to be at stopping the spread of malware and other attacks.

